Ok guys, let’s talk about ransomware in really simple terms…
To explain it simply, ransomware is a particularly evil type of attack that’s been going for about five years now. And it’s a VERY effective attack as well, and I’m going to show you why.
Essentially, you can think of ransomware as digital hostage taking. And it works very similar to how you might compromise your system with other attacks i.e. you click on a malicious link in an email, you download a malicious file by accident etc.
What the bad guys do is that once you have clicked the link/opened the file/visited a malicious website they basically scan your entire system, figure out what files are important to you, and then encrypt/scramble them so you cannot gain access to them anymore. We are talking about ALL of your pictures, your emails, Word documents – anything you’ve created that’s of value to you
But the attack doesn’t stop there!
Oh no…What happens next is what we call “adding insult to injury”: the ransomware hackers tell you that if you don’t pay them X amount of money by Y date, then you’re not going to get your files back….Ever.
So messed up, right??
Keep in mind also, the encryption they’re using is VERY strong, and not even the NSA can crack it (yeah, it’s that strong).
There will be a decryption key, but only the hackers have that key, and the only way you can get that key back to unlock all your files is if you pay them the ransom money (usually in some form of cryptocurrency).
Obviously you don’t want to pay them, because if you do, you’ve sent them a message that you’re willing to pay; what they will likely do is come back and encrypt even more stuff so they can get even more money from you.
And so you can see what these attacks look like, let me show you using a visual example.
Check this out: you’re at work one day, and you accidentally click on a malicious link in an email, not realize anything bad happened, and then continue going about your day (not knowing what’s now going on under the hood of your system). The next day you come into work, and see something like this on your computer screen:
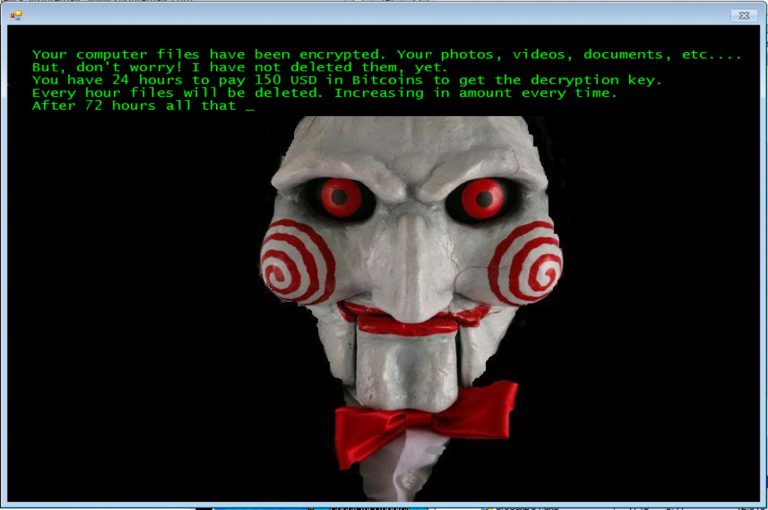
The scary message says, “YOUR FILES HAVE BEEN ENCRYPTED. Your photos and documents have all been compromised but don’t worry, we haven’t deleted them… YET. You have 24 hours to pay X amount in Bitcoins to get the decryption key.”
And these hackers mean it. They aren’t going to give you your files back unless you pay them that money.
Or what about this example:
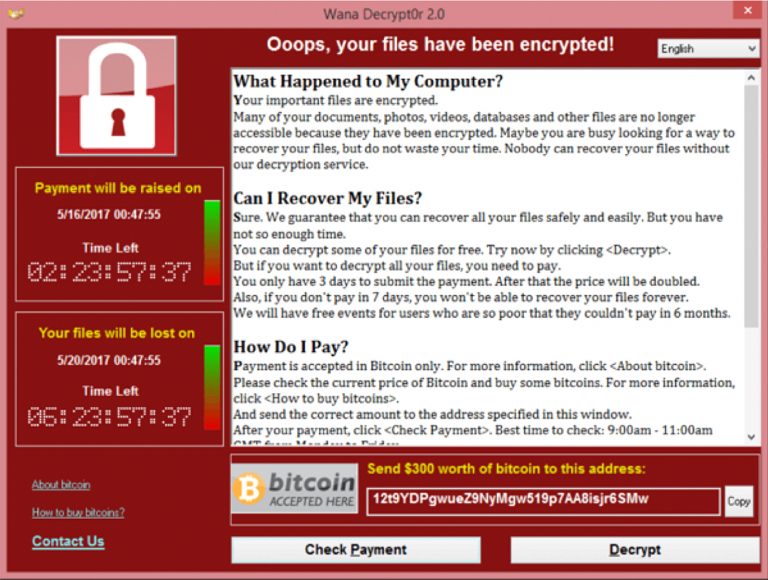
This one was actually very famous, and you may have heard about this on the news a few years ago. It’s called WannaCry (the attack literally made one want to cry in pain). It’s been since speculated that the North Korean government actually performed this attack, because their economy was in such a bad state. So they were sending this ransomware out, trying to get people to pay them money in order to keep their economy afloat!
The WannaCry ransomware hit about 100 countries, targeting hospitals, universities, and lots of businesses, and they were asking for about $300 in Bitcoin currency to get the ransomware removed from the infected systems.
Or what about this example:
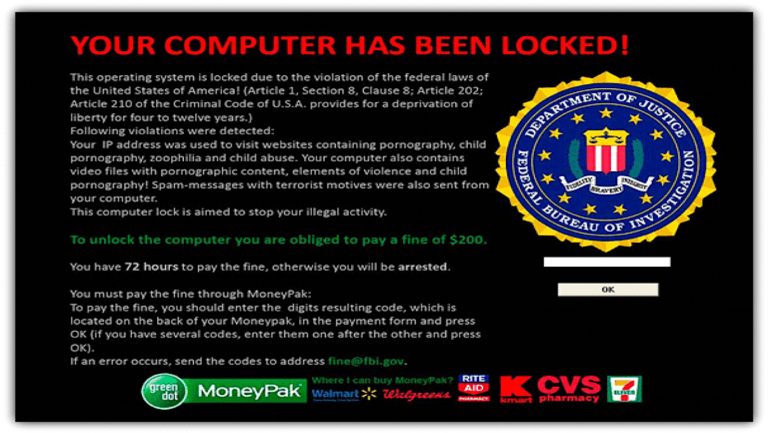
It even has a (obviously fake) official-looking Department of Justice/FBI logo on the top right to make it look real. And the message says that basically your computer’s unique IP address has been used to visit pornographic websites, and that you’re even sending ‘spam with terrorist motives’ (whatever that even means). Seriously, all of this is rubbish.
But they continue by saying “To unlock the computer, you are obliged to pay $200” (can you believe, it the FBI and DOJ will let you off for only $200!).
And then at the bottom they tell you to go to your local convenience store or supermarket and get a gift card for $200 and send it to them.
VERY IMPORTANT NOTE: no government agency, or law enforcement agency is going to ask you to pay for a ‘crime’ like this with a gift card. Please remember that anytime you receive a phone call, email or text message like this asking you to pay with a gift card, or some kind of Money Pak card from a super market or convenience store…It’s 100,000% a scam!
Do not go anywhere near this, it is rotten.
You might think this last example is rather silly (which it is), but unfortunately it works, because the hackers are preying on our emotions, particularly that of fear. They create a call to action, and pretend to be a figure of authority, so that we want to act immediately!
So now that I’ve showed some examples, here are your solutions, and it’s very simple.
First and foremost, make sure you have very good system ‘hygiene’ (I will write more on this in another blog post soon).
But at a minimum ensure that the following are patched and updated to the latest versions at all times:
Also make sure you NEVER CLICK on any link in any email, or download any file attachments unless you know for certain its benign (Maybe a bit easier said than done, but I will be blogging about this as well soon, so stay tuned :))
Moreover, keep your browsing to only reputable websites, especially at work (you don’t want to be the person known for introducing ransomware into your company network, right?) And obviously have a good anti-virus solution installed. Like I said, I’ll go in to a lot more detail on these and more in a new blog post very soon…
And what should you do to make sure you reduce the pain of having ransomware on any of your systems at home or work?

BAM! As simple as it sounds, you have to always have a GOOD backup copy of your most important files. If your system is compromised, you have to have a good offline backup. Period.
Storage is so cheap right now, so there really isn’t any excuse for you not to back up your files. By offline I mean you can have an external drive that you plug into your system periodically (say, once a week to backup, and disconnect right after, so ransomware never jumps on to the external drive).
And you should also back up into the ‘cloud’ as a secondary backup in case your external breaks for any reason. You can easily back up to your own iCloud account if you use Apple products, or you can back up to Google Drive, DropBox, Microsoft OneDrive, Box etc. It’s cheap and easy, so please backup your data.
When at work, your company should have a backup protocol in place to back up your data. If in doubt, please check with your IT team, and I’m sure they will set you up with one!
Its important to remember that with ransomware you only have 2.5 options:
Please be safe 1:M Secure out there everyone.
***
#ClickGameOver